Smooth and global identity verification
Our identity verification solutions help you prevent fraud and secure compliance with high conversion rates, keeping costs low.

Cost efficient
We offer global reach with very competitive pricing. Our solution also allows reaping the benefits of reusable customer identity once you have taken the initial onboarding cost, making it even more cost-efficient.
Conversion friendly
Automatic document capture, smooth UX and high usability gives you a smooth, fast and optimized customer experience with high success rate and perfect data where users are onboarded in 55 sec.
Secure identity
Stay safe from AI-driven fraud and its associated costs without impacting the experience for your customers. Protect against multiple fraud vectors with features such as device biometric verification, dynamic QR codes, liveness detection and document verification.
Privacy Protected
Complying with eIDAS 1 and 2, we offer a secure customer identity solution hosted within the EU. With encryption and stringent privacy measures, it adheres to EU data protection rules and extends compliance globally.

Onboard customers in 55 seconds
The process begins with document scanning or RFID reading, using optical character recognition to accurately extract data from ID documents from over 200 countries while enhancing assurance through cross-matching.
It then employs facial recognition and liveness checks for online ID verification, utilizing advanced technology and AI to combat fraud and detect compromised documents. Finally, a robust verification process ensures document authenticity, which is crucial for preventing identity fraud and maintaining security standards.
High quality data extraction
Visual Zone OCR
Extracts printed text from identity documents using Optical Character Recognition (OCR) technology to validate user details accurately and swiftly.
Barcode Reading
Deciphers encoded data from barcodes (like PDF417) on IDs, verifying authenticity by matching information against official records and standards.
MRZ Reading
Scans the Machine-Readable Zone (MRZ) on passports and IDs, quickly extracting essential details like name, DOB, and document number for verification.
RFID Reading
Reads embedded RFID chips in passports and IDs, extracting encrypted data directly from the chip for secure, tamper-proof identity validation.
Lexical Analysis
Analyzes and cross-references extracted text data to detect inconsistencies, errors, or potential fraud, ensuring data integrity and accuracy.
95
%Success rate
6500
Identity documents
95
%Automation rate
50
%Lower IDV cost
Contact our sales team
Are you ready?
Get in touch!
Ready to learn more?

Cost-efficient global coverage
Secure document verification
Document Liveness Detection (Holograms & Screenshot Check)
Detects genuine documents by verifying dynamic security features like holograms and ensuring documents aren't manipulated via screenshots or photos.
Data Cross-Checks
Compares data consistency across document sources: the Visual Zone, MRZ, Barcode, RFID-ensuring all extracted details align for accurate verification.
Automatic Authenticity Control
Automatically inspects security features, patterns, and data to detect counterfeits, ensuring documents meet standard authenticity benchmarks effortlessly.
RFID Server-Side Verification
Reads and verifies RFID data on secure servers, ensuring encrypted information matches stored records for enhanced, tamper-resistant identity validation.
Biometrics
A necessity for secure identity
Biometrics is essential for creating a secure identity because it relies on unique, inherent physical and behavioral traits-such as fingerprints, facial recognition, and voice patterns-that are nearly impossible to duplicate or forge. This significantly reduces the risk of identity fraud compared to traditional methods like passwords or ID cards, which can be easily stolen or tampered with.
Additionally, biometric data is difficult to replicate or lose, providing a reliable and convenient way to verify someone's identity quickly. Biometrics enhances security by linking identity to an individual’s unique features, making authentication more accurate, consistent, and resistant to unauthorized access.
1
Face Image Quality Assessment
Firstly we analyze the clarity, lighting, and focus of the captured image to ensure it meets quality standards for accurate recognition.
2
Face Attributes Evaluation
Following this we evaluate key facial features like eyes, nose, and jawline, verifying they are detectable and clear for reliable identification.
3
Liveness Detection
To avoid spoofing we check for signs of genuine presence and detect generative AI content to differentiate between real faces and spoof attempts like photos, videos or AI replicas.
4
Face Match 1:1 (Document Portrait and Selfie)
Finally, we compare the document mug shot to the selfie, to confirm both images belong to the same individual accurately.
Find your use case or industry
Truid is a complete digital identity verification solution that serves multiple industries and use cases.
Do you want to learn more about how our identity verification platform works in practice?
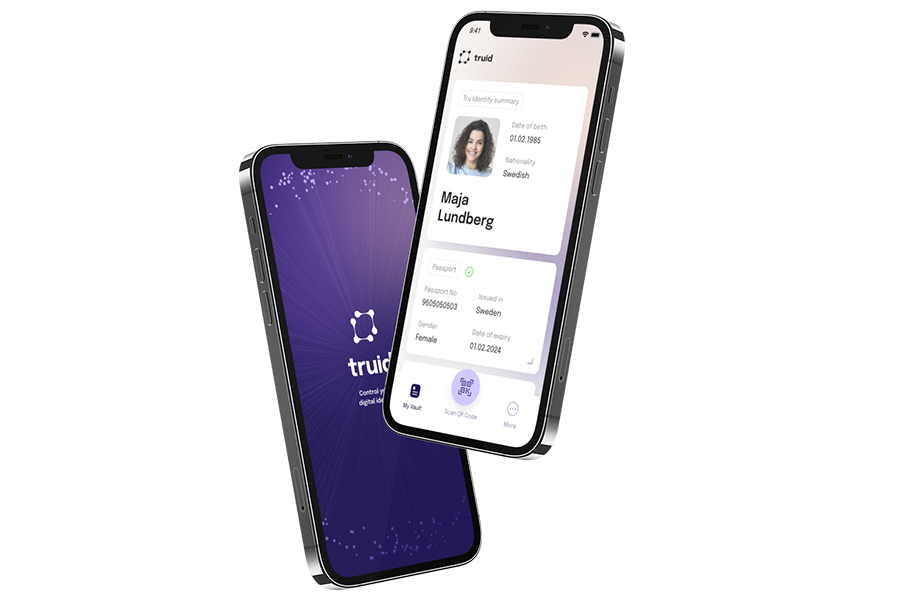
Verify users where they are
Integration options
Integrate smoothly with your operations
REST API
Our REST API enables smooth communication between systems using standard HTTP methods. It facilitates easy data exchange and gives you direct access to our functionality over the web, supporting a wide variety of integration scenarios.

Webhooks
We offer Webhooks to provide real-time data updates directly to your specified endpoint. This feature ensures you receive instant notifications and updates, allowing seamless integration and immediate response to events within your application.

OIDC (OpenID Connect)
For secure authentication, we support OIDC, which builds on OAuth 2.0. Selected by the EU in eIDAS2 as the future identity protocol. OIDC enables identity verification and safe access to users’ information, making it easier to manage authentication within your system.

No Code
Our no-code integration option is perfect for non-technical users, allowing you to build applications or automate workflows with visual tools and pre-built components—no programming required. It’s a fast, efficient way to leverage our solutions without deep technical expertise.
Verification made simple
Send and track requests instantly from your browser
Experience hassle-free identity verification with our user-friendly Identity Portal. Easily send and receive verification requests over email, all from a single web interface-no integration required.
Perfect for businesses with low-volume or occasional needs, our solution lets you manage verifications quickly and efficiently, saving time and effort. Click below to explore how the Identity Portal can simplify your workflow!
High assurance level
User identities with higher assurance levels provide a significant value by enhancing security, trust, and compliance in digital interactions. They ensure that the verified identities are genuine, accurate, and belong to the intended individuals, reducing risks related to fraud, identity theft, and unauthorized access.
This increased reliability not only safeguards sensitive information but also builds user confidence, streamlining processes and reducing friction in customer interactions, ultimately leading to better service experiences and operational efficiency.
Truid supports most global passports, ID cards, and driving licenses to eIDAS Substantial LoA. The most secure identities are based on documents equipped with a chip, verified with RFID and the NFC reader of the phone. We manage document scanning and validity controls primarily in partnership with Regula Forensics.
eIDAS
We comply with the EU’s eIDAS (Electronic Identification, Authentication and Trust Services) regulation, which sets standards for secure electronic identification and trust services, ensuring reliable cross-border digital transactions across Europe.
NIST 800-63-3
We adhere to NIST 800-63-3, a US standard that provides guidelines for digital identity verification and authentication, ensuring high levels of online security and user identity protection.
GPG-45 (Good Practice Guide 45)
Our processes meet the UK's GPG-45 standard, defining rigorous identity verification practices and proofing levels to guarantee accurate and trustworthy identification.
ISO/IEC 29115
We follow the ISO/IEC 29115 standard, which establishes a global framework for identity assurance, ensuring our authentication methods meet international security and risk management guidelines.
Care about your users
Assisted scan
Challenges It Solves for the User
Assisted Scan simplifies the verification process by minimizing errors during document capture. Users no longer need to worry about blurry images, incorrect angles, or poor lighting. This reduces frustration and makes the identity verification process faster and more intuitive.
Advantages for the Service Provider
For service providers, Assisted Scan improves the accuracy and reliability of data extraction, reducing manual interventions and rejections. This leads to higher pass rates, faster verification, and lower operational costs. Additionally, it enhances user experience, leading to better conversion rates and customer satisfaction.
Truid's Integration of Assisted Scan
Truid utilizes Assisted Scan in all our identity verification flows, ensuring that users have a seamless and accurate verification experience every time. This commitment enhances both security and convenience, benefiting both users and service providers.
Competitive pricing for businesses of all sizes
Customer voices
The impact of Truid’s identity verification
“Really easy to integrate technically and easy to get support with the Truid team for our developers, who are also located in different parts of the world.”
Document management
CEO
"Truid helps verify our customers of any nationality within minutes and is responsive to our feedback, adjusting the product accordingly."
E-commerce
CEO
"The IDV process for the user has very good UX and opts for fast conversion."
E-sign platform
CEO
"Truid is the only good solution we've found that we can use to identify foreign customers."
Proptech
CEO
FAQs
How does online identity verification services work?
- Data Collection: The user submits personal information and documents, like a passport or driver's license, through the platform.
- Document Verification: The platform uses technology to authenticate the documents, ensuring they are legitimate and untampered.
- Biometric Verification: The user may be asked to provide a selfie or video, which is compared to the ID document using facial recognition and liveness detection.
- Database Cross-Referencing: The system checks the user data against government records, watchlists, and other databases to ensure accuracy and compliance.
- Result Delivery: The verification result is provided to your company, confirming the user identity or highlighting issues.
- Secure Storage: All data is securely stored, ensuring compliance with regulations like GDPR.
How does Truid guarantee digital trust and security?
Truid fosters digital trust and security with its cutting-edge identity management approach. By leveraging decentralized identity, Truid strengthens security by distributing and encrypting user data, reducing the risk of centralized weaknesses and ensuring tamper-proof records.
The platform uses zero-knowledge proof protocols, allowing secure authentication without revealing sensitive information. With advanced consent management and interoperability, Truid gives users full control over their digital identities, offering a powerful solution for the safe and reliable management of personal information.



